Penetration Testing Methodology
If you are having a penetration test carried out for the first time, it makes sense to take a closer look at the specific procedure. To get the most out of a penetration test, you should prepare and plan the test. A few contractual agreements are also necessary. We have therefore summarized the key steps for you here.
Planning the Penetration Test
A penetration test should be carefully prepared in order to achieve the desired objectives. It is therefore worth asking yourself several questions.
Why is a penetration test carried out?
A penetration test can be carried out for various reasons. The most important reason is to have the information security checked by a neutral third party in order to improve the overall security level. Another reason may be that a penetration test is required by auditors, cybersecurity insurers or customers. In this case, confirmation of information security after the penetration test is often also required. Especially as proof for a cybersecurity insurance policy, it can be useful to have a checklist of the required requirements in addition to the penetration test, which are specifically checked.
Which parts of the infrastructure should be tested?
In a penetration test, the entire infrastructure or just individual servers can be tested. You should also check which systems should be explicitly excluded from the penetration test in order to avoid disruptions to operations or production. Embedded systems in particular are sometimes very sensitive and can hang up or crash. The effects of a penetration test should therefore be carefully examined.
Who is commissioned?
A penetration test should be carried out by experienced testers. Certifications, e.g. OSCP or CEH, are a possible, but perhaps not the only decisive criterion. The quality and validity of the report and the recommended security measures are also important. The best penetration test is of no use if you cannot derive suitable security measures from it.
Legal Framework
A penetration test should also be secured on a legal level with suitable agreements.
Declaration of Consent
With the declaration of consent, you give us your permission to attack your systems. In the declaration of consent, you can specify which systems and IP addresses may be attacked and which are expressly excluded from attacks, and denial-of-service attacks are also usually excluded.
Social engineering attacks are not included in a purely technical penetration test, but can also be commissioned. In this case, please note that the consent of the works or staff council is usually required. The data protection officer should also be involved in the preparations.
Confidentiality Agreement
Be sure that we never pass on information from penetration tests and delete any data obtained that is no longer required after the final report. The confidentiality agreement gives you additional assurance that we will handle the information obtained in the penetration test reliably and confidentially.
Exemption from Liability
We require an indemnity against liability for consequential damage for which we are not responsible. This can be important, for example, if service providers who look after your systems have not been informed and therefore terminate contracts, resulting in additional costs for you. However, this can also be relevant if a system is damaged by the penetration test and your backups were faulty and therefore damage occurs.
Data Processing Agreement
In many penetration tests, we succeed in capturing personal data, e.g. login names, email addresses or even passwords. This is, of course, personal data that we process on your behalf in accordance with the GDPR. If there is a risk that we will receive personal data, a data processing agreement should also be concluded. As a rule, a data processing agreement can only be waived for penetration tests that are carried out exclusively on test or development systems and, if applicable, for tests exclusively via the Internet. If you have a standard processing agreement for all suppliers, we will also be happy to accept your agreement.
Purchase Order
All we need now is your order and then the penetration test can begin.
Penetration Testing Procedure
Our procedure for carrying out a penetration test is basically structured according to the following scheme, which is also recommended by the German Federal Office for Information Security (BSI):
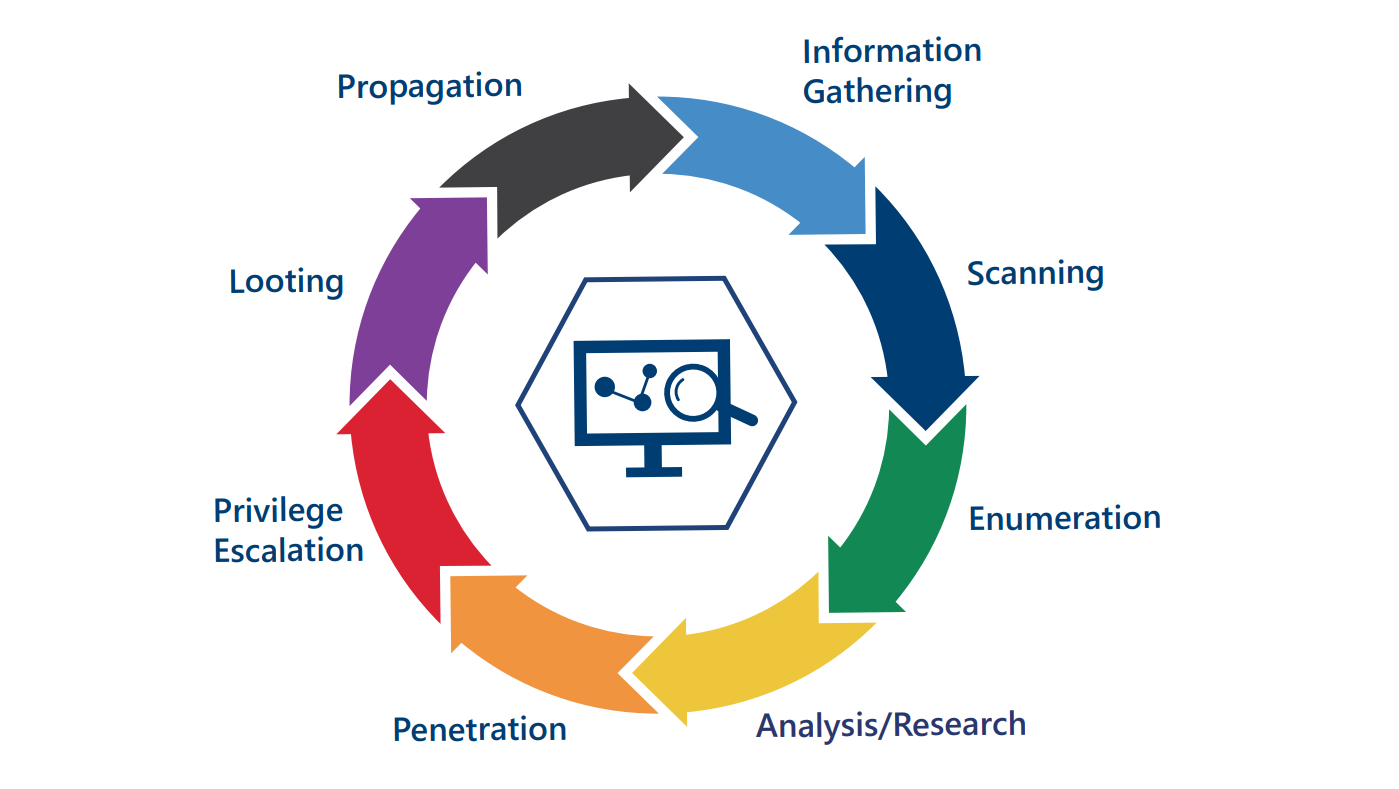
1. Searching for Information about the Target System
Computers accessible on the Internet must have an official IP address. Freely accessible databases provide information about IP address blocks assigned to an organization. Search engines are also a popular source of inadvertently published confidential data.
2. Scanning the Target Systems for Services
The entire network is checked with a port scanner, whereby open ports allow conclusions to be drawn about the assigned applications. Initial conclusions about security can be drawn from the active systems found and the open ports.
3. Vulnerability Scanning
Mit verschiedenen Vulnerability Scannern sowie speziellen Web Application Scannern werden die Systeme auf mögliche Schwachstellen hin untersucht.
4. Vulnerability Exploitation
Any vulnerabilities found can be used to gain unauthorized access to the system or to prepare further attacks. This unauthorized intrusion is referred to as "penetration".
5. Privilege Escalation and Further Steps
Once a system has been penetrated, rights are usually escalated in order to gain privileged access. A real attacker could then extract data or use the system as a springboard for further attacks.
Closing Report
We document and evaluate all penetration test results in detail and in a comprehensible manner. You can use our risk assessment and cost estimate to prioritize measures. We present our findings to you in a management presentation.
More Questions?
Schedule a date with us. We would be happy to present our penetration tests and our approach to you in detail.