Forensis Analysis in the Cloud
The use of cloud services has not only fundamentally changed IT itself, but has also led to new challenges in specific areas of information security. In particular, the forensic analysis of attacks and security incidents when using cloud services requires a fundamentally different approach to traditional forensic analysis with physical access to IT systems and storage media.
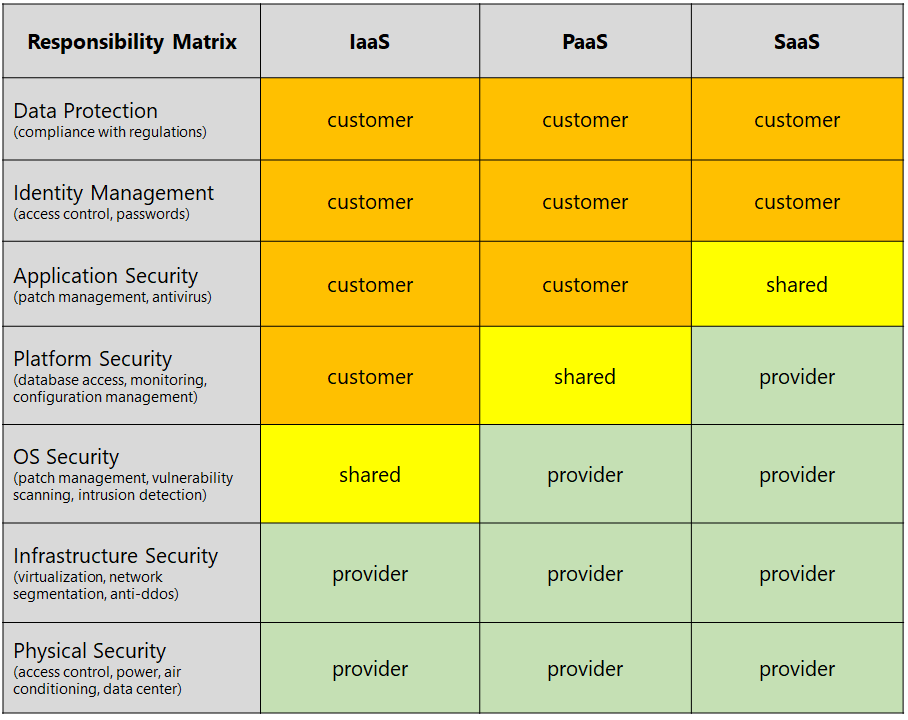
Cloud Computing Service Models
When using cloud services, a distinction is usually made between three models: IaaS (Infrastructure as a Service), PaaS (Platform as a Service) and SaaS (Software as a Service). Special forms such as SECaaS (Security as a Service) or VoIPaaS (Voice over IP as a Service) are not taken into account here.
- Infrastructure as a Service: In IaaS, the cloud provider primarily provides hardware and virtualization. The operating system and all applications are installed and operated by the customer. A large part of the responsibility for information security therefore remains with the customer. The cloud provider is solely responsible for physical security and virtualization security.
- Platform as a Service: With PaaS, the cloud provider provides the customer with a development platform for web services. As a rule, customers no longer have control over the operating system, so this responsibility is transferred to the provider.
- Software as a Service: In SaaS, the customer uses an application that is operated entirely by the cloud provider. Responsibility for the security of the hardware, operating system and application therefore lies entirely with the provider.
The following diagram shows a possible distribution of responsibility.
Challenges of Forensic Analysis
The forensic analysis of cloud services is characterized in particular by the following challenges.
Separation of data and metadata
In the forensic analysis of cloud-based systems, a very fundamental problem arises from the fact that the data concerned and the associated metadata are stored and managed in different places. Metadata includes, for example, file owners, access authorizations, timestamps of the last change and the last access and other information such as the account and IP address of the last access. On normal data carriers, owners, access authorizations and time stamps are stored directly with the data itself in the file system and can be evaluated together. However, data about the account and IP address of the last accesses does not exist at all. In cloud services, the data is stored independently of metadata and possibly distributed on different data carriers or even in different data centers. Metadata must then be taken from the administration database or from server log files.
An IT forensic analysis of a security incident of a cloud service cannot be carried out independently by the customer, as the customer generally does not have access to the administration database and the server log files.
Lack of Tools
Various commercial (e.g. EnCase, X-Ways) and open source (e.g. Autopsy, Sleuth Kit) tools exist for the forensic analysis of data carriers, which support all common file systems and file formats and enable simple evaluation of the data found.
There is a lack of suitable tools for forensic analysis that enable simple import of data and log files and clear evaluation.
Missing Standards
While there are comprehensive recommendations, regulations and standards for traditional forensic analysis, such as the IT forensics guidelines from the Federal Office for Information Security in Germany, there are no such guidelines for cloud services. The BSI guidelines date back to 2011 and naturally do not yet take cloud services into account. The ISO/IEC 27037 standard "Guidelines for identification, collection, acquisition and preservation of digital evidence" from 2012 does not help either.
On the other hand, there is also a lack of standards and uniform formats for log files. Some cloud providers issue log files in CSV format, others use text files in syslog format, and some log files are also stored in databases. The scope of the logged data is also inconsistent. While the client IP address, logged-in user and timestamp are typically logged by all providers, further information is sometimes missing, e.g. on the type of login, the browser used, the client operating system, etc. In some cases, actions can be traced. In some cases, actions can be traced, but important information for identifying the attackers is missing.
Different Jurisdictions
A further problem is posed by different jurisdictions with sometimes very different legal systems. Actions that are punishable in one country are only considered misdemeanors in another country or are not even criminally relevant. If data is stored by a cloud provider in a jurisdiction with a different legal system, it can be problematic to obtain the necessary data and log files for the forensic analysis of incidents. Even official requests for information often do not help.
Our Service
We advise and support you in analyzing attacks and security incidents in the cloud. We help you to request the necessary data, protocols and log files from your cloud provider and support you in evaluating this data.
If necessary, we can also help you report data breaches in accordance with Article 33 GDPR and prepare a criminal complaint.