Web Application Penetration Testing
A web application penetration test is a penetration test that specifically targets web applications and web service APIs. Web applications are now used for many business-critical services and are therefore a primary target for attackers.
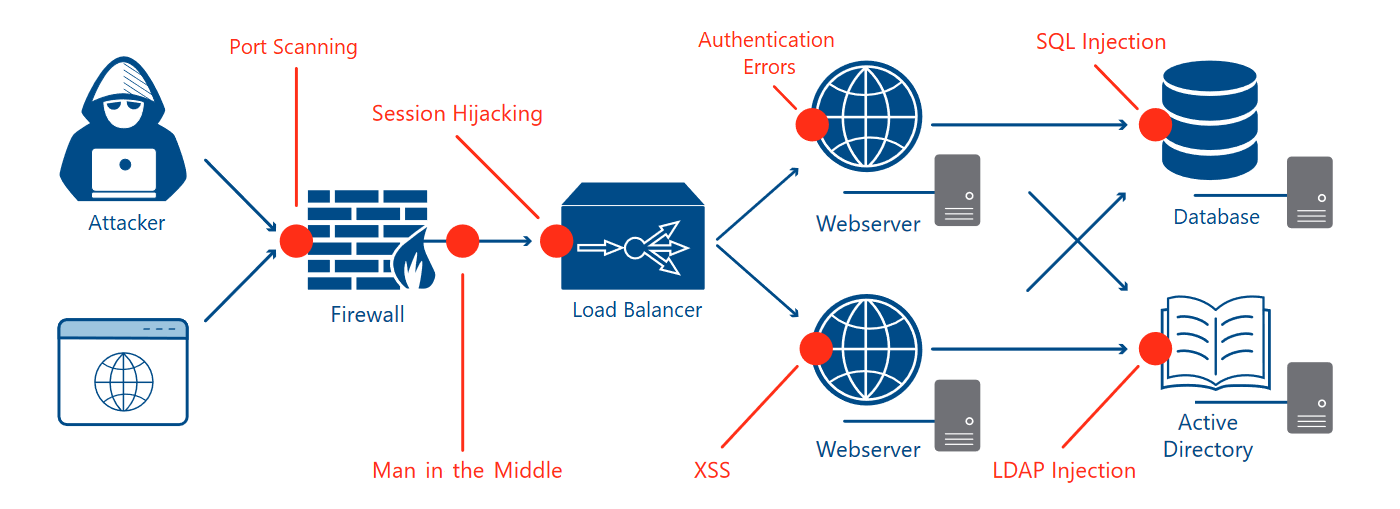
OWASP Top 10 Web Application Risiks
The Open Web Application Security Project (OWASP) is an internationally active non-profit organization that has set itself the goal of improving the security of web applications and web-based services. OWASP is aimed in particular at the developers of web applications and attempts to sensitize them to information security.
At not entirely regular intervals, most recently in 2021, OWASP publishes a list of what it considers to be the ten biggest risks.
- A01:2021 – Broken Access Control
- A02:2021 – Cryptographic Failures
- A03:2021 – Injection
- A04:2021 – Insecure Design
- A05:2021 – Security Misconfiguration
- A06:2021 – Vulnerable and Outdated Components
- A07:2021 – Identification and Authentication Failures
- A08:2021 – Software and Data Integrity Failures
- A09:2021 – Security Logging and Monitoring Failures
- A10:2021 – Server-Side Request Forgery (SSRF)
A central component of every penetration test against a web application is therefore the testing of the top 10 risks. However, a complete penetration test must not be limited to these 10 points.
Web Application Penetration Testing Methodology
A standardized approach is recommended to systematically identify errors and vulnerabilities. We use the Web Security Testing Guide (WSTG), also developed by OWASP, which is available in a published version 4.2 and a development version 5.0 as of 2023. The WSTG contains 12 sub-chapters with topics that should be tested in a penetration test.
- Information Gathering
- Configuration and Deployment Management Testing
- Identity Management Testing
- Authentication Testing
- Authorization Testing
- Session Management Testing
- Input Validation Testing
- Testing for Error Handling
- Testing for Weak Cryptography
- Business Logic Testing
- Client-side Testing
- API Testing
Depending on the desired test depth and agreed test scope, the individual test points from these chapters can be verified to varying degrees.
Web Services and Web APIs
Security risks not only occur in classic web applications and web stores that can be operated with a browser. Web service APIs that provide data as XML or JSON are also increasingly being used. The front end may be an application created in JavaScript in the browser, a mobile app on a smartphone or another application in microservice architectures, for example.
Web APIs have their own risks and dangers and should therefore be checked just as extensively and carefully as classic web applications.
What does a web application penetration test cost?
The costs of a web application penetration test depend in particular on the size and complexity of the web application as well as the desired or required depth of testing. A simple customer portal naturally requires less time for testing than a data protection-critical application in which sensitive personal data is processed or a web store in which credit cards are used for payment.
It is therefore best if you briefly present your application to us and together we can determine the testing effort and depth of testing. Simply make an appointment with us.
Your Benefit
In our penetration test, we uncover vulnerabilities and security gaps in your web application before the attackers do. This ensures that your data is protected in the best possible way.
For each vulnerability found, you will receive a detailed report with evidence and recommendations for remedying and improving security.
In addition, you will receive a certificate of the penetration test carried out, which confirms the security of your application to you or your customers, if necessary, after a follow-up test.