Cloud-based Shadow-IT
Traditionally, "shadow IT" refers to IT systems or software that are operated alongside the official IT infrastructure. In other words, without the knowledge or at least without the support of the IT department. Shadow IT is associated with typical risks such as a lack of backups, breaches of license conditions, outdated software, a lack of virus protection and compatibility risks.
However, the topic of shadow IT is relatively new in connection with cloud-based applications.
More than Dropbox
Many IT managers think of cloud-based shadow IT primarily as services such as Dropbox or WhatsApp, i.e. systems that are used for the unauthorized exchange of data and entail risks for the confidentiality of this data and for data protection.
In fact, the problem is much bigger today.
It is now no longer unlikely that an individual department will use a cloud service that can be quickly rented to solve a specific problem, even without involving the IT department, for example to analyze data or perform special calculations.
This starts with a simple Nextcloud server rented from a hoster, but does not end with the use of Slack or Basecamp by an entire department. In particular, the possibility of using these services with private cell phones makes them both attractive and dangerous.
Risks from Cloud-based Shadow IT
Even if the data itself is protected, there are legal risks if, for example, personal data is transferred to systems outside the EU or contractual agreements on the use of data or confidentiality agreements are breached as a result.
Basically, all typical security risks from cloud usage come into question.
- Violation of compliance rules within the company
- Loss of confidentiality of sensitive data
- Data loss due to lack of data protection/backups
- Violation of statutory data protection regulations
- Lock-in due to lack of data export options from the cloud
In contrast to regular authorized use, however, there is no compliance check by the information security officer and no data protection by the IT department.
Our Approach
Shadow IT does not "just happen", but is often caused by user or departmental requirements that are not solved quickly and efficiently enough by IT, at least from the user's perspective. It can also simply be caused by poor communication when users simply feel thwarted by new ideas or opportunities.
Experts often use a 3-phase model to resolve shadow IT, which can also be used in a similar form for cloud-based shadow IT.
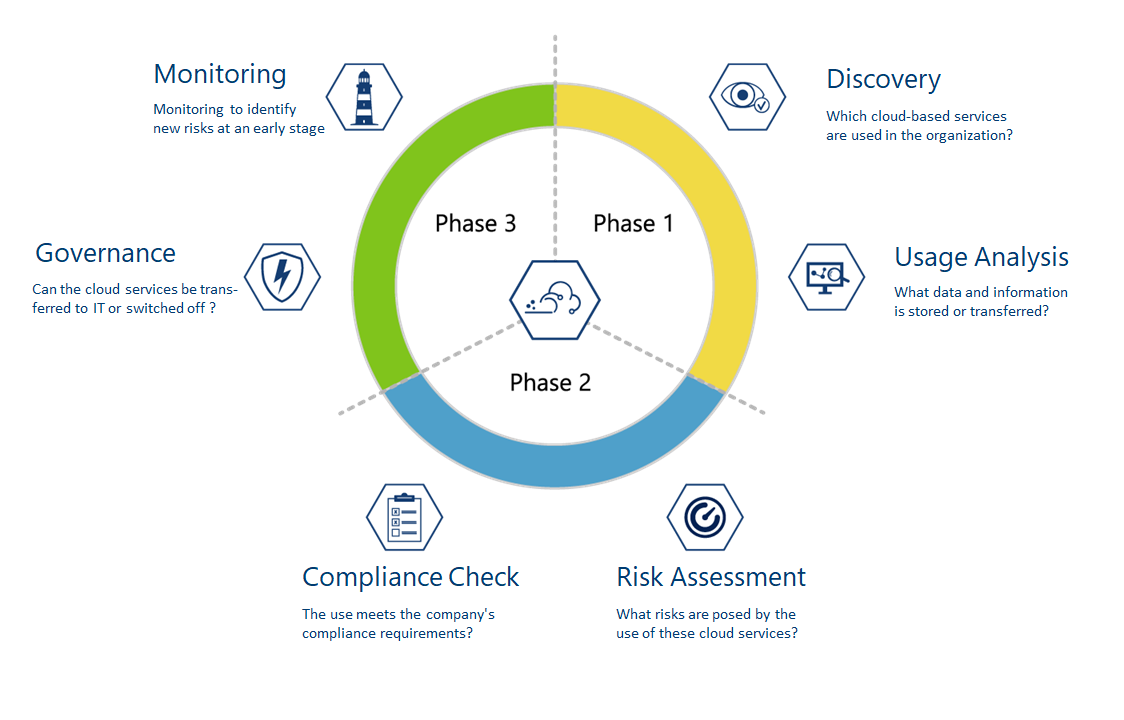
Phase 1
Discovery: Identify which cloud-based services are used in the company. Firewall or proxy log files, for example, are helpful here, as are interviews with the responsible department heads. The problem here is that there are now over 15,000 commercially usable cloud services.
Usage analysis: Before carrying out a risk assessment, it is important to check how these cloud services are used, i.e. which data and information is stored or transferred, which devices are used to access them and which internal and external users have access.
Phase 2
Risk Assessment: Our risk assessment identifies the risks associated with the use of these cloud services for the company. A large number of risk factors must be taken into account, such as data loss, violation of laws or industry-specific regulations, data protection breaches, etc. The risk can be summarized in a risk score.
Compliance Check: Parallel to the risk assessment, it should be checked whether the cloud service used meets the company's compliance requirements or can at least be used in this way. In addition to legal requirements such as the GDPR, these compliance requirements also include special industry-specific requirements, e.g. in the financial sector or requirements due to necessary certifications such as PCI-DSS.
Phase 3
Governance: In this context, governance means either integrating the cloud services used into the company infrastructure, i.e. adoption by IT, connection to identity management (SSO), securing the services, e.g. through two-factor authentication and backup, etc., or shutting down the services and transferring the required data to the company IT.
Monitoring: Continuous monitoring of newly offered and risky cloud services in order to identify potential threats at an early stage. On the other hand, use within the company in order to detect newly commissioned shadow IT.
Data Sources
We use all data sources that you can provide us with:
- Microsoft Cloud App Security and Cloud Discovery
- Log files from firewalls from various manufacturers
- Log files from proxies from various manufacturers
- Data from a SIEM
- Netflow version 5 or version 9 (RFC 3954) with collector
- PCAP traffic recordings
Of course, data that has already been processed is particularly helpful. For example, many firewalls with Next Generation or Deep Inspection already support a fairly precise evaluation of the cloud apps used. Proxy systems with TLS/SSL interception also generally have the option of precisely evaluating the data traffic.
Our Service
We examine your infrastructure and find the shadow IT used in your company. We carry out a usage analysis for you and help you to assess the risks specifically for your company and your business model. In particular, we will also take your industry-specific requirements into account.
If necessary, we will help you configure your systems to generate the necessary log files, e.g. through SSL interception, or configure your SIEM to record and evaluate the required log files.
We advise your IT on the takeover and regular operation of cloud-based shadow IT or recommend shutting it down if necessary.
We support you in the implementation of monitoring and security measures.