Breach and Attack Simulation (BAS)
Breach and Attack Simulation (BAS) enables companies to check the detection capability of their infrastructure through automated tests of threat vectors. With a BAS, both external and internal threats, e.g. lateral movement and data exfiltration, as well as a complete portfolio of other attacks from the MITRE ATT&CK matrix can be simulated without causing any damage. In particular, the effectiveness of Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR) as well as Security Information and Event Management (SIEM) and even the Security Operations Center (SOC) can be verified. In addition, the BAS generates detailed reports on security vulnerabilities and prioritizes remediation measures based on the risk level. A breach and attack simulation is therefore a useful addition to penetration tests and red teaming, even if it cannot completely replace them.
Manual Simulation
Manual simulations are essentially penetration tests, but not with the primary aim of penetrating systems, but with the aim of triggering alarm systems. With manually compiled tests, a very large scope of possible attacks can be carried out very realistically, but with correspondingly high personnel and time expenditure. In practice, manual simulations are therefore only useful as part of a product launch, e.g. dedicated attack detection or after the introduction of a SOC. Only through automation is a regular, e.g. monthly, review of attack detection practicable.
Automated simulation
A major disadvantage of manual simulations is that regular testing cannot take place for reasons of time and cost. However, additional IOCs, an update of the SIEM platform or new employees in the SOC can significantly change the detection rate in a short period of time.
In security-sensitive environments, for example in critical infrastructures or when particularly sensitive data is processed, tests should therefore be carried out not just once but on a recurring basis. Continuous simulations in particular serve to detect weaknesses at an early stage and maintain the security level.
Automating the breach and attack simulation offers important advantages here:
- Automation is what makes continuous simulation and therefore constant monitoring of security measures possible in the first place.
- Exact reproducibility of the attacks can ensure that the results of different tests are reliably comparable. With manually performed attacks, the risk of deviations leading to falsified results is naturally higher.
- Thanks to the improved comparability, reproducible and therefore relevant key figures for information security can be automatically derived from the breach and attack simulation.
Traffic-generating breach and attack simulation
Traffic-generating BAS software generates artificial data traffic, either from recorded PCAP files from recorded attacks or between virtual machines that serve as attackers and attack targets. The log files and events obtained show which attacks are detected and how attackers could move around the network undetected.
Agent-based Breach and Attack Simulation
Agent-based BAS software is the most common form of breach and attack simulation. Agents are installed on various clients and servers in the LAN. Based on these agents, further attacks such as lateral movement or data leakage are initiated. Unlike a vulnerability scanner, the system does not search for specific vulnerabilities. Instead, further potential attack vectors are tested.
Cloud-based BAS
BAS software operated in the cloud is most comparable to a real attack. It can simulate various attacks, particularly against the company's access points. Different entry points into the network can be used simultaneously with different attack vectors. Cloud-based BAS is usually provided as Software-as-a-Service and can therefore be introduced very quickly with little effort.
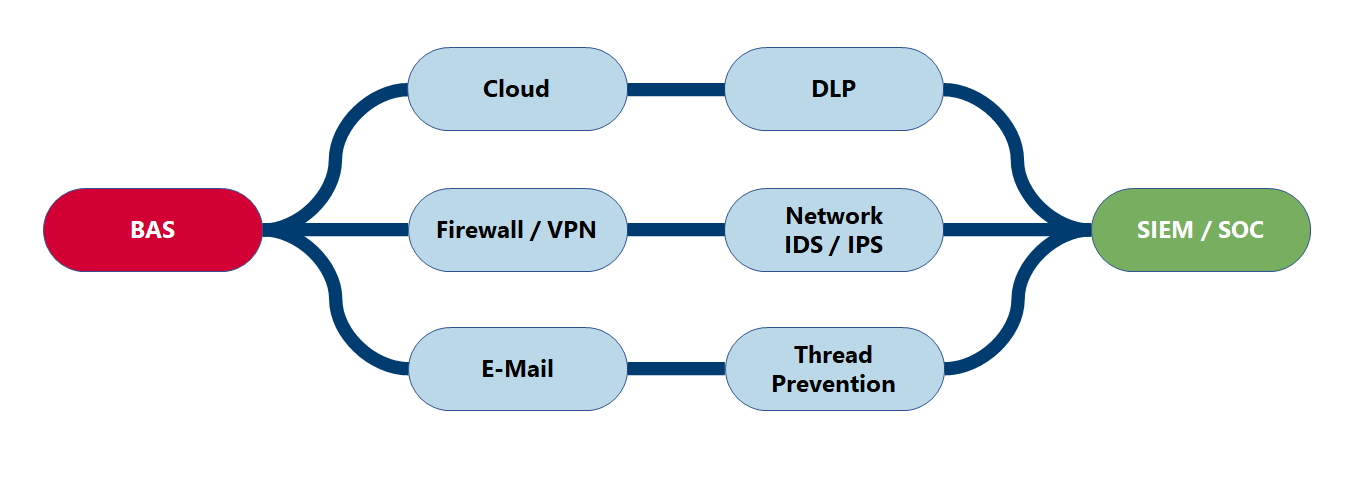
Boundary Posture Management (BPM)
Boundary Posture Management is a variant of Breach and Attack Simulation. It primarily checks protection against attacks from outside and protection against data leakage from inside. For example, e-mail-based attacks or attacks against VPN access can be carried out from the outside. From the inside, connections to command & control servers are established, data is forwarded via DNS and ICMP and other attacks are simulated. The BPM can be used to verify the existing attack detection in particular, but also data leak prevention (DLP).
Why BAS?
The introduction of a BAS solution can make sense for several reasons.
In the area of critical infrastructures, the BSI Act § 8a paragraph 1a requires KRITIS operators to use systems for attack detection. The effectiveness of such systems can then be tested using a BAS or BPM, for example.
If particularly sensitive data is processed, e.g. special personal data in the healthcare or financial sector, a BAS can be used to identify and rectify potential weaknesses at an early stage.
ISO 27001:2022 requires the introduction of data leak prevention as a new control. Here, too, the functionality of the DLP can be checked regularly and automatically with a BPM.
Our Service
We implement an effective breach and attack simulation for your organization. We work with you to define your requirements and select the appropriate product. We integrate the selected BAS solution into your infrastructure and customize the reports to your requirements.